Issues and Solutions¶
Unable to Add new Devices or List the Device Types¶
When facing the issue, that when creating a new Device in the IE Management, the following Message appears:
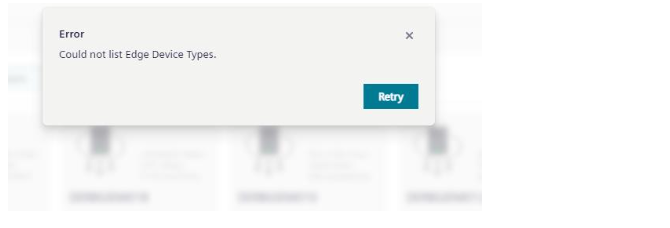
It could be, that the client configuration of the ie-management is not correct.
To check and to fix, please go to the Identity and Access Management Service and select under Clients the ie-management
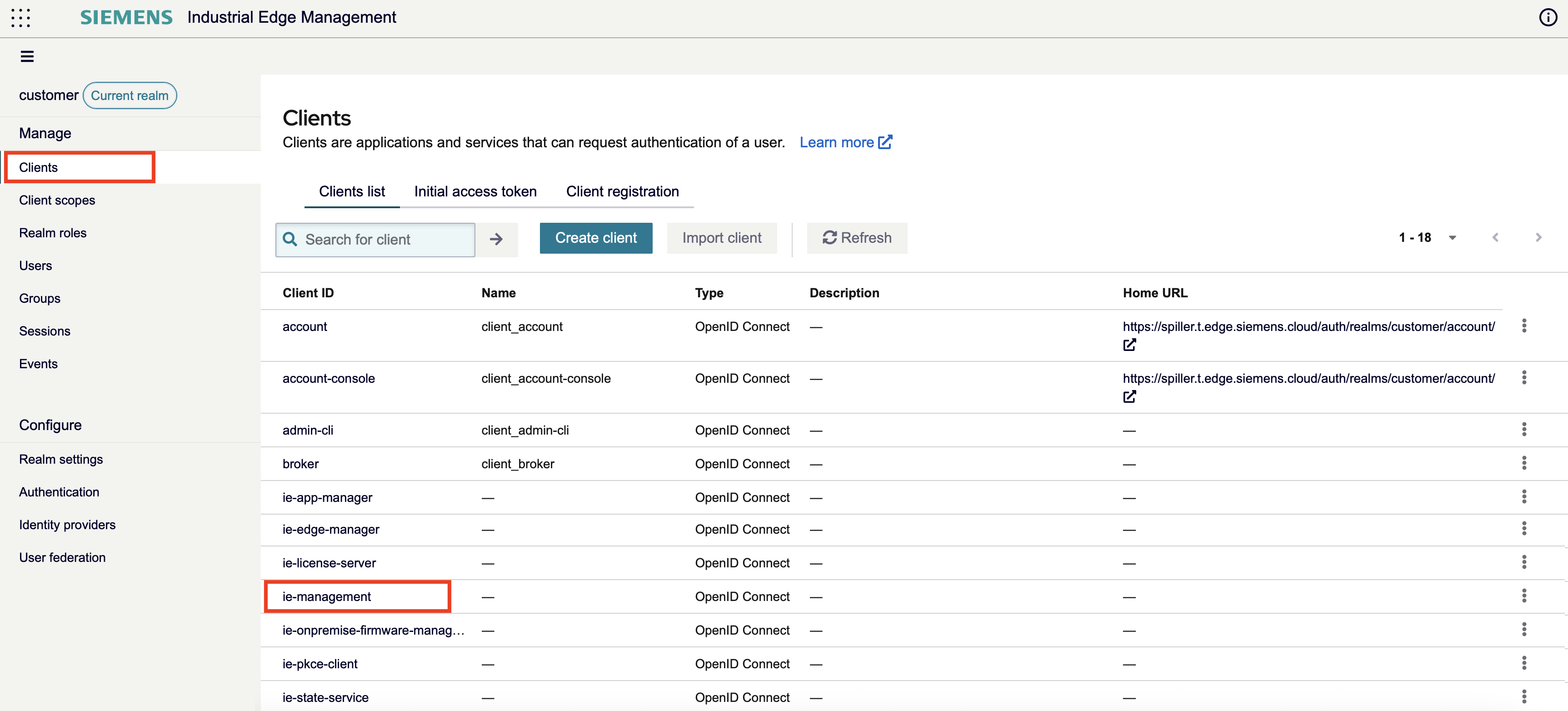
Go to the Tab Client scope and check if there is a Scope available roles
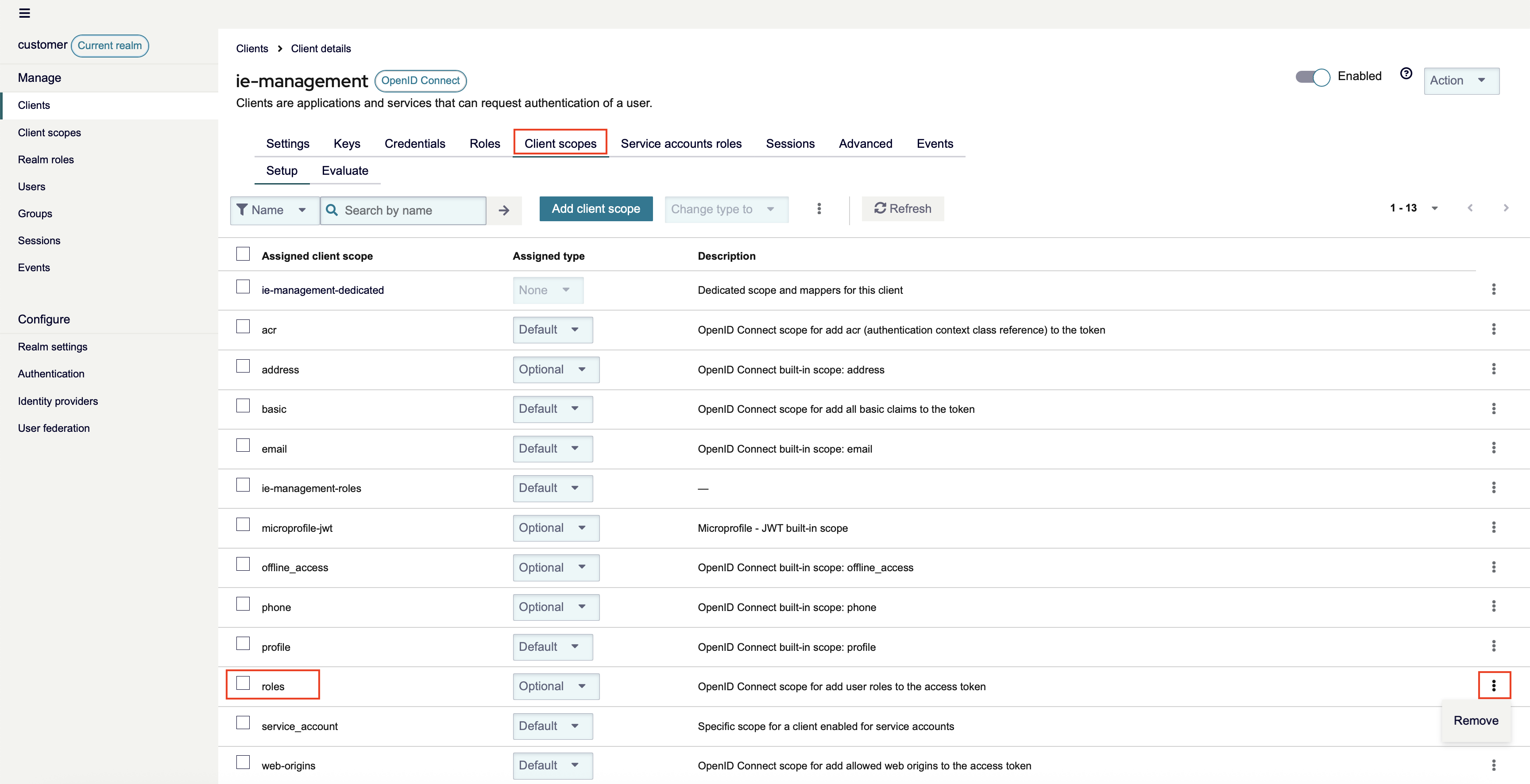
If this scope is listed, you can safely remove it, by clicking on the three dots and select delete.
SameSite=None setting in Keycloak Cookie¶
Keycloak is using the setting SameSite=None in the cookies (KEYCLOAK_IDENTITY, etc.)
Setting SameSite=Strict would break any application that is not hosted on the same eTLD+1 as Keycloak. Browsers do not send cookies with SameSite=Strict after a redirect to Keycloak if the original site is on a different eTLD+1.
The major risk behind this issue is mitigated by the following:
- Keycloak utilizes other mechanisms for protection against CSRF attacks, built into the OIDC and SAML protocols for application interactions
- Except of legacy all cookies are marked with the HttpOnly and Secure flags.The HttpOnly flag prevents client-side scripts from accessing cookies, reducing the risk of session hijacking. The Secure flag ensures that cookies are only sent over encrypted connections (HTTPS), protecting them from interception
- Addition: In the upcoming Keycloak Version Legacy Cookies will be removed
Access Token Lifespan¶
Default Configuration¶
The access token lifespan is set to 6 hours by default. This extended duration is specifically designed to support long-running background operations, such as:
- Creating system backups
- Restoring from backups
- Installing applications
- Performing system updates
Background Operations¶
During these operations:
- Actions continue running in the background
- The user's access token is used to authenticate subsequent operations
- Operations may span several hours to complete
Important Notice¶
The default token lifespan is an integral part of our validated quality assurance scenarios.
NOTICE
Reducing the token lifespan below the default value of 6 hours may:
- Interrupt long-running operations
- Cause background tasks to fail
- Lead to inconsistent backup states
We cannot guarantee successful completion of all system operations if the token lifespan is decreased from its default value.