Roles in Keycloak¶
It is possible to grant users access to the IEM and "User groups" / "Admin groups" via roles in Keycloak.
Mapping Users to Group Roles and Default Roles¶
Add default group to users¶
You can also create a new group with the same Role Mappings.
To do this, navigate to Groups and create a new group.
First you need to give the group a name.
After that, you can also set Role Mappings for this group.
Click on the group name in the group list. Switch to the Role mapping tab and click on Assign role.
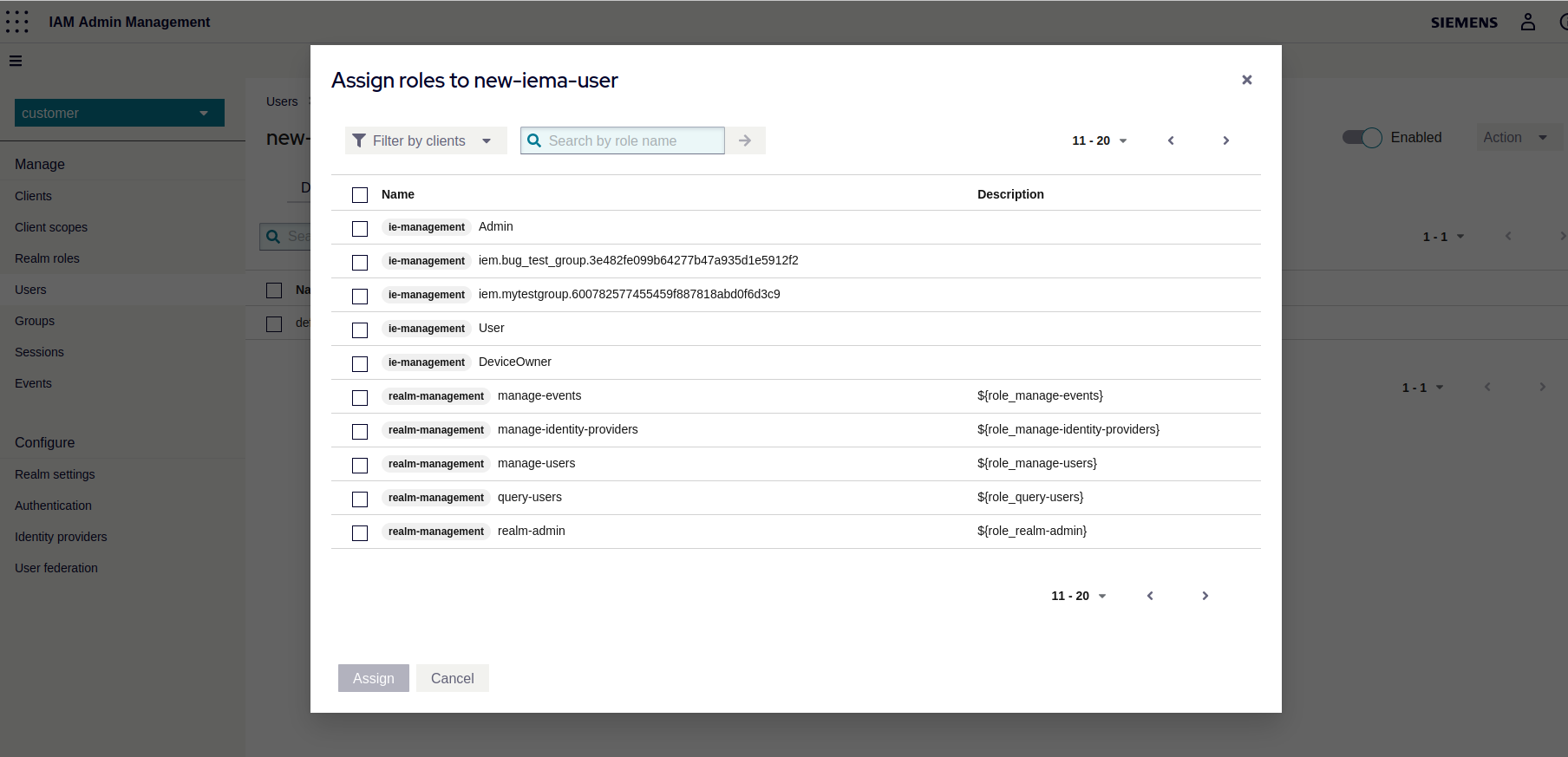
Switch the filter to Filter by clients and select from that list the roles you want to assign. The roles for the Industrial Edge Management App have the client id ie-management. After clicking Assign the selected roles will be assigned to the group.
Now you can add this group to the Default Groups.
Go to Realm settings and switch to the User registration tab. Select Default groups and select the group you created from the list. Click on Add.
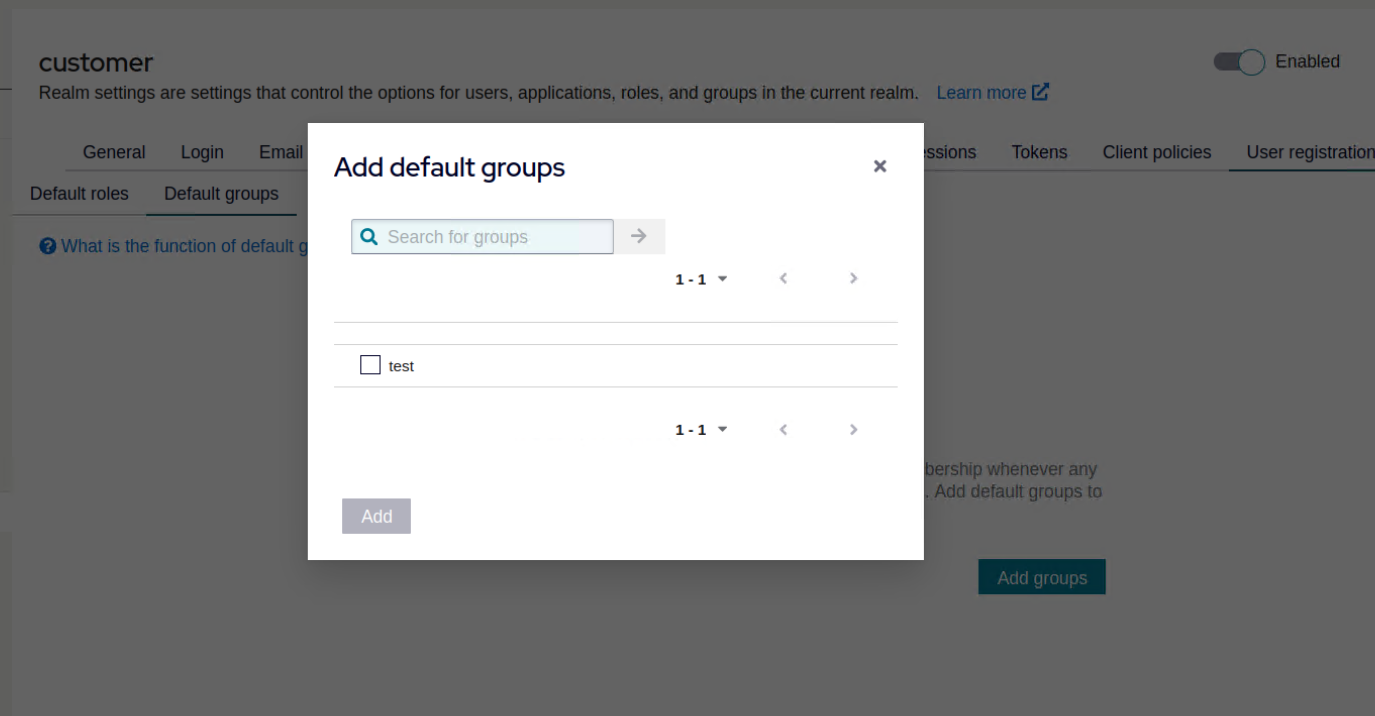
Any new user will be a member of this default group and will have the added roles.
IEM roles and groups¶
IEM Roles¶
There are three IEM roles
- Admin
- User
- DeviceOwner
see Assign role
The role Device Owner should be assigned additionally to a user with either User or Admin role.
Admin¶
The Admin role gives IAM users access to the Edge Management, Edge Management Admin, and Application Manager. Additionally, it makes the “Identity & Access Management” tile visible. The Admin role includes all the permissions of the User role, as well as additional service-specific permissions.
User¶
The User role gives IAM user access to the Edge management. It enables users to create and manage their own resources, such as devices and apps. Additionally, it serves as a prerequisite for accessing the app catalog.
DeviceOwner¶
The DeviceOwner role is useful for users who need access to all IEDs.
With the DeviceOwner role, the user can access all devices even if they didn't onboard them themselves and the devices are not shared by groups.
The DeviceOwner role allows the user to do anything with the device that the original onboarder of the device can do.
A user with this role can view/modify jobs, install applications, view installed applications and device statistics, and more for all devices.
A user with this role can add/remove all devices to/from all existing My Admin groups. It doesn't matter if the user created these groups or if the user is a member of the group.
NOTICE
It only affects the "My Admin" groups in the IEM and not "My User" groups in IEM or "My Admin" groups in Industrial Edge Management App.
Once the DeviceOwner role is removed the user only sees their own devices and groups or the devices that are shared with them.
NOTICE
Limitations
DeviceOwner role.DeviceOwner role can't create labels if they haven't activate a device yet.App Projects with the DeviceOwner role the app has to be shared with the creator of the device also.Permissions of DeviceOwner Role¶
Below table lists permissions available for DeviceOwner role:
| Action | DeviceOwner |
|---|---|
| Device Export | ✓ |
| Device Import | ✓ |
| Device Delete | ✓ |
| Device List | ✓ |
| Device Relocation | ✓ |
| Application Install | ✓ |
| Application Restart | ✓ |
| Application Start | ✓ |
| Application stop | ✓ |
| Application uninstall | ✓ |
| Application Configuration Update | ✓ |
| Application Configuration Delete | ✓ |
| List Installed Application | ✓ |
| Application Details | ✓ |
| Device Manage Labels | ✓ |
| Device Backup | ✓ |
| Device Restore | ✓ |
| Device Reset | ✓ |
| Device Hard Reset | ✓ |
| Device Reboot | ✓ |
| Device Remote Access | ✓ |
| Device Shut Down | ✓ |
| Device Update | ✓ |
| Device Log | ✓ |
| Device Statistics | ✓ |
| Device Discovery | ✓ |
| Device Tag Add | ✓ |
| Device Tag Delete | ✓ |
| Device Tag List | ✓ |
| Groups Add | ✓ |
| Groups Update | ✓ |
| Groups Delete | ✓ |
| Install Job List | ✓ |
| Install Delete | ✓ |
| Install Edit | ✓ |
In addition to the above mentioned IEM roles, additional roles are created in Keycloak corresponding to user groups and admin groups in IEM.
The role name that is generated from the group name : iem.<groupname>.<groupid> (e.g. "iem.myusergroup.fae4601bea73485b8298a48ebdfaa3d9")
Device Owner role limitations¶
Manage Device Tags
The Device Owner Role has permissions to manage the Device Tags, this includes, creating, removing and updating tags. However the DeviceOwner role can only manage tags by accessing the quick actions menu of the device. Managing tags at the edge device detail page, is not available with the DeviceOwner role.
Custom roles via IEM Groups¶
Create Groups¶
Log into the IEM https://<iem_ip>/pp/ and create a new group under Groups -> My User Groups or My Admin Groups.
Select the permissions you want to give the group and enter a name.
A role iem.<groupname>.<groupid> is automatically generated in the customer realm for every created group. To give the user access to the group, assign this role to the user.
NOTICE
The user creating the group will automatically be assigned the new role. If it was a My Admin Groups devices added to that group will also appear in the "Authorized Edge Devices" view for that user as long as the user has this role.
Remove groups¶
Log into the IEM https://<iem_ip>/pp/ and select the group under Groups -> My User Groups or My Admin Groups.
Click on the Edit icon and then click on Delete.
How to recover a deleted role in Keycloak¶
There is no way to restore a deleted role in Keycloak. You need to recreate it.
To do this, select the Identity & Access Management tile in the Launchpad or open the Keycloak Admin Console at https://<iem_ip>/auth/admin/customer/console/ and log in as admin.
Select Clients → ie-management → Roles → Create role
and enter the name of the role and click save.
The role name follows this schema:
iem.<group name>.<group id>
You can then reassign the role to users to grant them the group permissions.
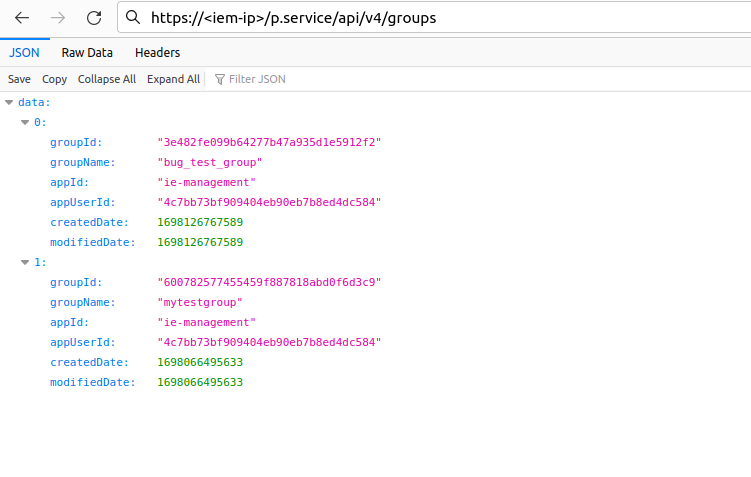
Group Name and Group ID¶
The user who originally created the group must log in and visit the following page.
https://<iem_ip>/p.service/api/v4/groups
It lists all the groups the user has created with their group names and ids. Check the list of groups for the one that corresponds to the deleted Keycloak role.