App Security¶
Protection of self-developed apps¶
Customers are responsible for implementing all required security measures protecting their self-developed apps with regard to security, and for preventing unauthorized access to their own apps by applying suitable access control measures to their exposed application workload.
Access control of self-developed apps¶
Customers are responsible for the access control of each developed app and for preventing unauthorized access to their apps. This applies to device-internal app-to-app communication and communication from/to services running outside the device.
Data protection¶
In Industrial Edge, customers have the possibility to store data outside of Edge Devices such as in their backend services running for instance on cloud infrastructure operated by the customer.
Customers are responsible for the confidentiality, integrity and availability (CIA) of data stored outside of Industrial Edge Devices and for preventing unauthorized access to the stored data.
Encrypted communication between Edge Apps¶
Customers are responsible for implementing encrypted and secure communication channels (e.g., HTTPS using TLS 1.2) for their apps.
Secure exposure of app communication¶
To secure the exposure of apps to the outer world, apps can use the platform provided reverse proxy.
Apps may directly expose communication interfaces by passing the proxy. In that case, the app needs to secure the communication properly.
Ephemeral (random) ports exposed by applications should be confined to the secure boundaries of the Industrial Edge Device — for example, for local WebUI, local engineering or debugging purposes.
App secrets and other confidential information¶
Application-specific secrets (passwords, tokens, private keys) must NOT be stored inside the
container images belonging to an Industrial Edge App.
They must also NOT be in the docker-compose file.
They should be stored in the app-specific cfg-data directory or any other persisted volume on the
Industrial Edge Device.
Access credentials required for accessing an app or by an app must be created as
device-specific credentials and must NOT be shared via multiple devices.
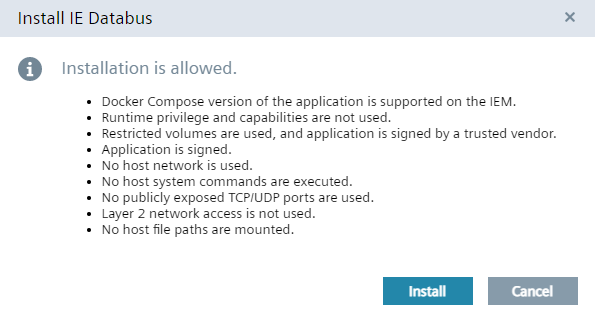
App installation information warnings¶
Customers can install any app on their IEM. To help keeping the system secure, a warning is showed when installing the app. Problematic app capabilities such as privileges, open ports and the app signature state are here visible.
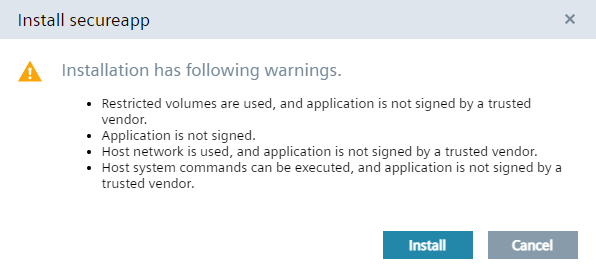
Non-critical apps also show any app information.