Technical Overview of IAM¶
Key Use Cases¶
- IAM with RBAC support as foundation service for the platform.
- Coarse Grained Access based on Resource Groups.
- OIDC with Authorization Grand Flow between Gateway and Auth Server (Keycloak).
Component View¶
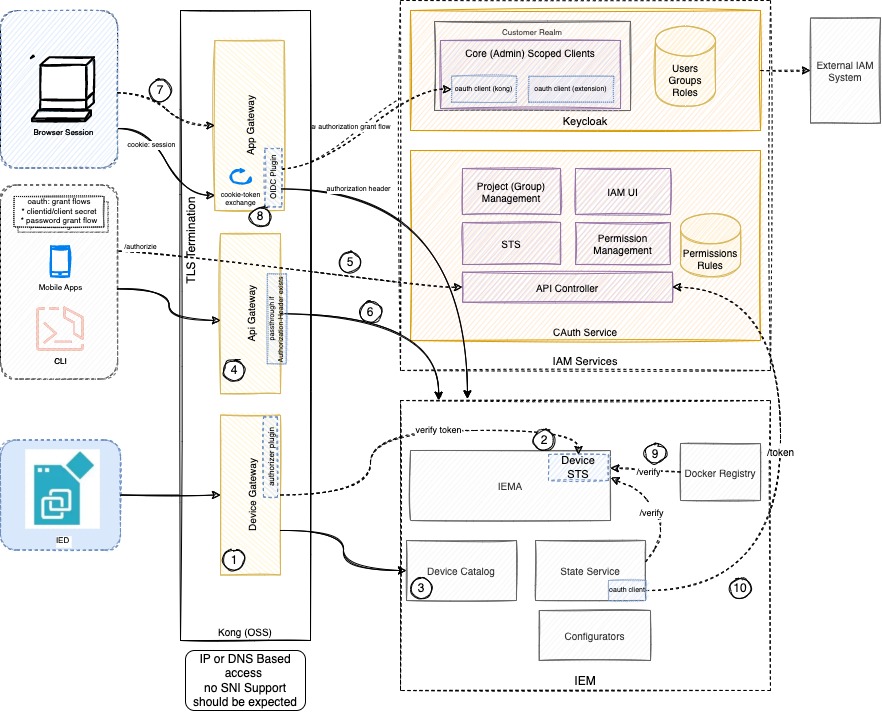
| No | Components | Description |
|---|---|---|
| ① | Device Gateway function | Device Gateway are multiple routes within the gateway managing the traffic for devices. This partially includes token exchanges with a kong plugin. |
| ② | Device Authentication | The requests of device are forwarded to IEMA, IEMA is using public key of to validate the device token. |
| ③ | Device Catalog | |
| ④ | API Gateway | API Gateway are specific routes to reach out to APIs of backend services. API Gateway is performing a token exchange if a cookie is provided. |
| ⑤⑥ | Transparent Mode of API Gateway | API Gateway is proxying the api requests to the backend without validating the authentication. For API Requests, this is the responsibility of the Backend Services. |
| ⑦ | App Gateway | App Gateway is receiving the UI/Browser traffic and is enforcing authentication by redirecting to IAM System (Keycloak). |
| ⑧ | OIDC Plugin | App/API Gateway uses a custom OIDC plugin (written in Lua) that authenticates and sets the cookie with session information. |
Relations¶
Flows¶
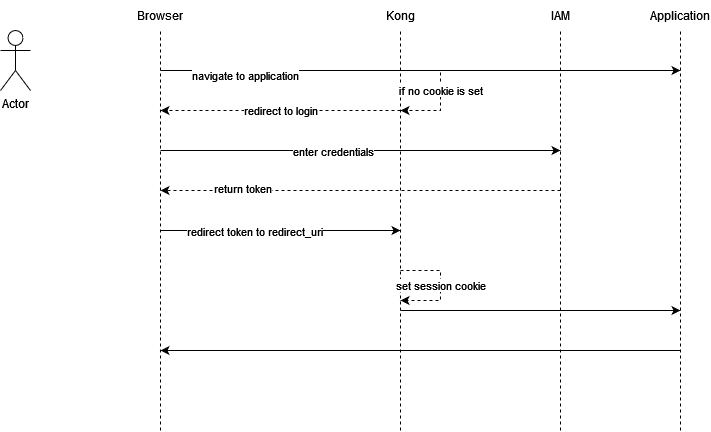
Login Flow¶
Service 2 Service¶
For API Access, it is possible to register additional clients in the IAM. Steps to use client to get access_token for API access Register Client Activate service account * Assign client roles to the service account
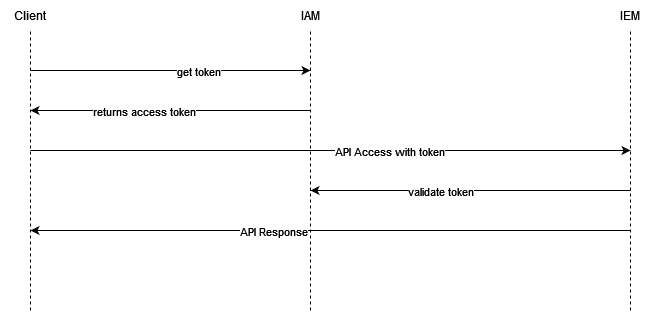
At the moment the Access is limited to the Admin Role of the IEM
Example:
curl --location --request POST 'https://<iem_ip>/auth/realms/customer/protocol/openid-connect/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=client_credentials' \
--data-urlencode 'client_id=<cliend_id>' \
--data-urlencode 'client_secret=<client_secret>'
{
"access_token": "eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICI2bm9NQVg3MjJwRVFSb2FQcFlLSUtlODVhQXpZSkVqY1gzeFd0cUtWOVgwIn0.eyJleHAiOjE2NjQ5OTUxMjEsImlhdCI6MTY2NDk3MzUyMSwianRpIjoiYjUxYTE0N2EtOTFkNy00NzM2LWJkYzktOTA3M2EyNzcwODZkIiwiaXNzIjoiaHR0cHM6Ly8xOTIuMTY4LjQ5LjIvYXV0aC9yZWFsbXMvY3VzdG9tZXIiLCJhdWQiOiI0MWZmNzNjOTcxOWE0MmJkYjAzNDgzNTUxMTRjZWI4MiIsInN1YiI6ImNiMTI4YzI1LTNhZTAtNGQ0ZS1hYWFkLTk4ZDE3ODM1MzgzMCIsInR5cCI6IkJlYXJlciIsImF6cCI6InRlc3QyIiwiYWNyIjoiMSIsInJlYWxtX2FjY2VzcyI6eyJyb2xlcyI6WyJvZmZsaW5lX2FjY2VzcyIsInVtYV9hdXRob3JpemF0aW9uIiwiZGVmYXVsdC1yb2xlcy1jdXN0b21lciJdfSwic2NvcGUiOiJlbWFpbCBwcm9maWxlIiwiZW1haWxfdmVyaWZpZWQiOmZhbHNlLCJjbGllbnRJZCI6InRlc3QyIiwiY2xpZW50SG9zdCI6IjE5Mi4xNjguNDkuMSIsInByZWZlcnJlZF91c2VybmFtZSI6InNlcnZpY2UtYWNjb3VudC10ZXN0MiIsImNsaWVudEFkZHJlc3MiOiIxOTIuMTY4LjQ5LjEifQ.XfdSd0O0vTQmVEbzSZlXmoHYhlPWgTg8oes8Gs9Dn_M6AVkomwweXhL6psx3V2T3_yzLnZhtf5kCsHgjLwk80AEhrdmbQsAmwuAl7EF8s4MMBocIeO-hp5F2JkylAX3nbF5iqP9_Ecjjht4O4ilLLKjKtFKPcRkXFEgzNxekfGt6adH0v5dGIMd8DLVFpJq5UMM7wtbMusTuXRP_SeX1Y1AnCRkM0j-smGWYpbEIE-rax-UAyiaznU9Q87JoOXG75Q5_xiC0BTI8Gb8wpoI99lAFZO6Gp4iCR0iPEHLVQErW58cj26dxObHoMk9OTNq-UL4LPdOcRgbuNRhU9pq6eQ",
"expires_in": 21600,
"refresh_expires_in": 0,
"token_type": "Bearer",
"not-before-policy": 0,
"scope": "email profile"
}