IAM - Overview¶
IAM (Identity and Access Management) provides core functionality for managing users, roles, groups, permissions, service2service authentication, authorization and the gateway. It is based on open source components (Keycloak and Kong). Some facade components exist for legacy reasons.
Authentication¶
The IAM uniquely identify and authenticate all human users. For UI access this is enforced by the gateway. For API requests, the backend service ensures authentication of the user.
Login and Logout¶
User can login to IEM using the launchpad url. The User can enter his username or email and password and click Login.
The user can logout by clicking on the logout button in the OS-bar.
Details on API-based Logins can be found in the following documentation:
Keycloak documentation: OIDC layers
IECTL documentation: configuration for IEM
API authentication how-to: API Authentication
User Info¶
The logged in user's details can be obtained by clicking on the user info icon on the OS-bar.
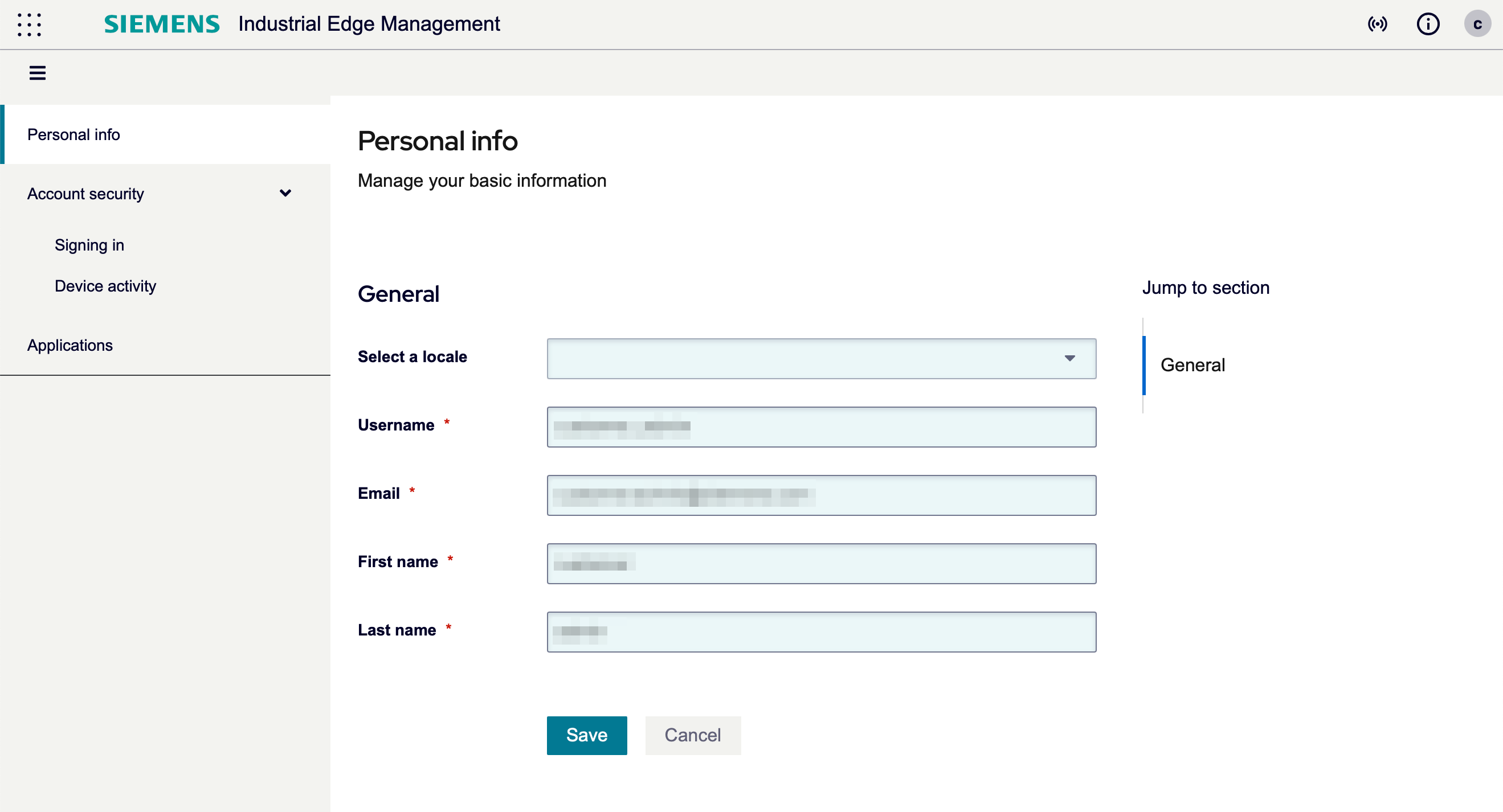
Account Management¶
The user can update his account details by clicking on the the user icon on the OS-bar and selecting Account Management.
IEM Users¶
Upon successful deployment of the IEM, two users are automatically created: the System Admin and the IEM Admin. These users are initially set with default values for their username and email, but users have the option to configure these values during the installation process.
System Admin¶
The System Admin user is responsible for managing the customer realm. This user is created with the default username customer_admin and an automatically generated password. In addition to having administrative rights in the IEM, this user also has the ability to manage Keycloak settings within the customer realm.
IEM Admin¶
The IEM Admin user is the intended user for the IEM. By default, this user is created with the username iem_user and an automatically generated password. This user is enabled for the IEM and holds the administrator role for the Industrial Edge Management App. While this user is enabled by default, it can be disabled during the installation process by setting the flag --set central-auth.keycloak.initialUser.enabled=false. More detailed instructions on configuring users and passwords during installation can be found in the Configure Users and Passwords for the First Installation section.
Keycloak¶
Keycloak is the underlying open source software of the Industrial Edge Identity and Access Management. The following pages describe the use of Keycloak in Industrial Edge Management. More detailed information can be found in the official Keycloak documentation.
| Name | HTML Link |
|---|---|
| Official Keycloak documentation | v 26.3 |
| REST API documentation | v 26.3.2 |
| CLI tool documentation | v 26.3.2 |
| Downloadable Keycloak archive | v 26.3.2 |
Keycloak Sidebar Overview¶
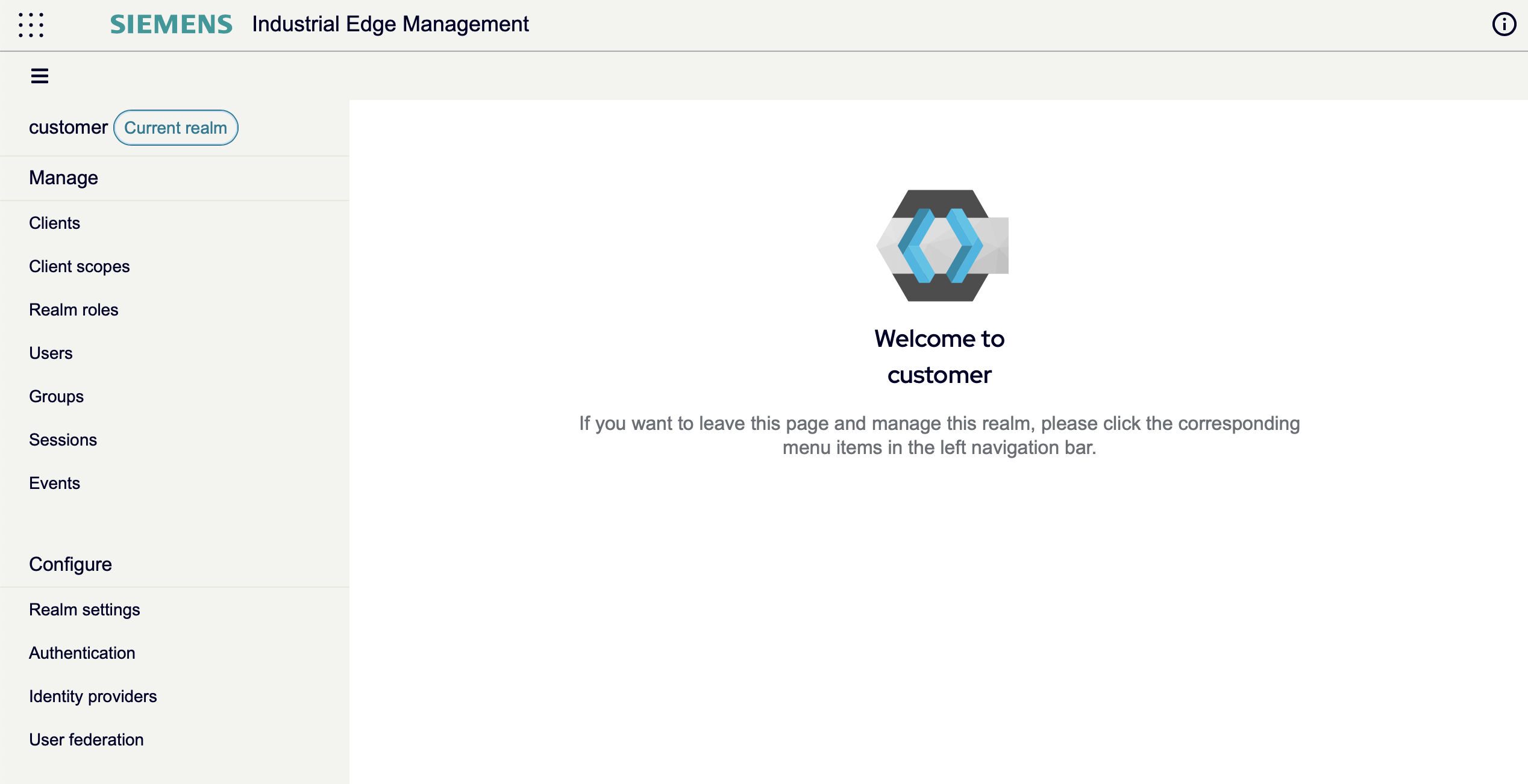
If the user is logged in as customer_admin, he will be able to access customer realm admin console by clicking on Identity and Access Management icon on launchpad. The user will see various options to manage clients, realm roles, users, groups, sessions, events etc. The user can also configure authentication and identity providers or change realm settings here.
Realm¶
Users, credentials, roles, and groups within the IEM are managed by realms. A realm is responsible for managing the authentication and authorization of users. Each user is assigned to a specific realm, which they can log into. Different realms can coexist simultaneously and are isolated from each other. Each realm can only manage and authenticate users within its own control. However, it's worth mentioning that the IEM does not support additional realms and is specifically configured to work with the Customer realm.
When the IEM is deployed, a default realm called the Customer realm is automatically created.
NOTICE
Do not change anything that is automatically created in the Customer realm. Otherwise, the IEM may not work properly.
NOTICE
The following Keycloak features do not work with the IAM:
- Remember me
- Impersonation
- Representation of Admin events